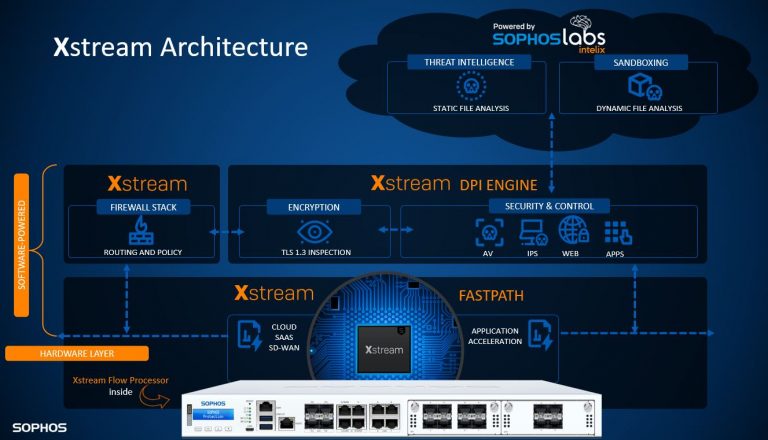
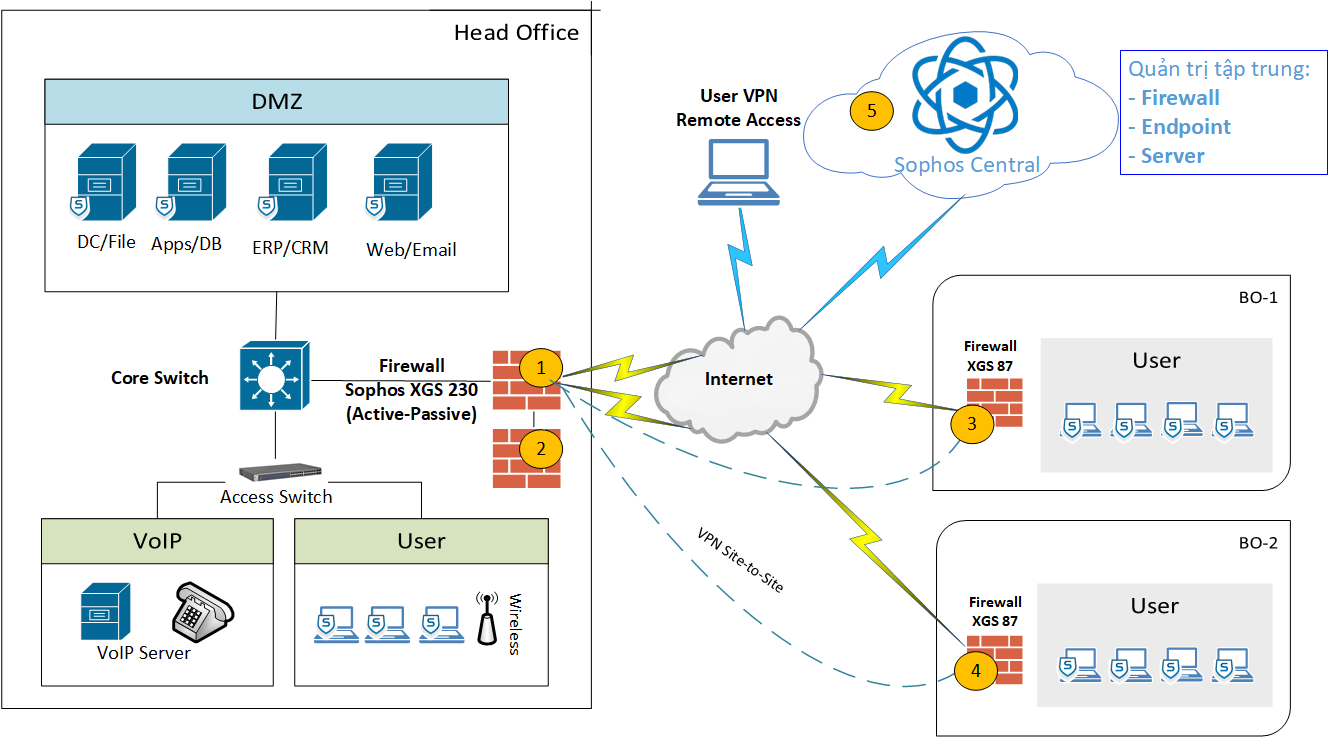
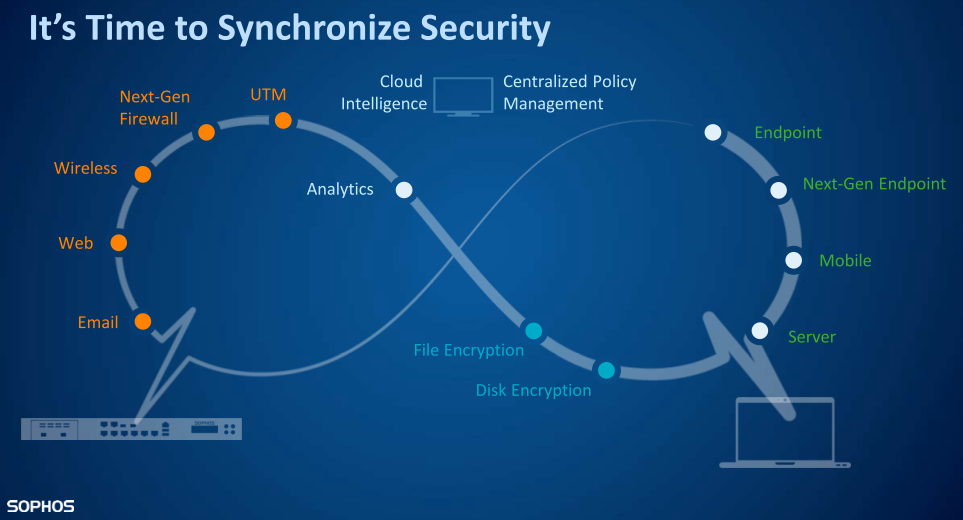
General requirements for information security systems
- Information security solutions must meet the ability to protect information in many aspects. Information must be available, complete and confidential, at any potential risk.
- Applying technology is not only concerned with its brand and reputation, but also has to consider the aspect of applying technology to the actual situation, whether it is appropriate and brings real effectiveness.
- Possibility to expand the feature in the future. Security risks are always developing complexly, so the chosen technology must match the trend of world technology.
- Choose popular technologies, have many support teams right away, and have a certain number of users.
- The selected solution and technology must be concerned with management methods, user-friendliness, and easy centralized administration because of large-scale deployment and wide-area networks.
- The system must meet the requirements at a reasonable cost, reuse the existing equipment, and must ensure the investment value for a long time from 3 to 5 years.
- The system must use devices (hardware and software) that ensure compliance with international standards, avoid using local technologies (hardware will be difficult to find replacement devices, software will be difficult to develop and integrate with other systems)
- The information security system can affect the entire information system when there is a problem, so the after-sales support and troubleshooting support of the good brands is also a criterion that is considered by the company

 Tiếng Việt
Tiếng Việt